Main section
PKI – what is public key infrastructure?
What is a public key infrastructure (PKI)? The basis of SSL/TLS certificates, digital signatures and more – for digital security and efficiency within companies
Summary
PKI is based on asymmetric cryptographic methods, meaning it involves the use of a key pair consisting of a private key and a public key. Aside from the encryption itself, the technology is also used to authenticate and sign documents and data. It is implemented using structures with a hierarchical arrangement. Certificates issued by the certification authorities bind a registered identity to a public key. Certificates have a validity period, but can also be revoked before they expire. Laws and standards specify the requirements for PKI, for example, regarding the use of certificates on the internet to secure web servers or email traffic.
Definitions relating to PKI
-
Confidentiality means that information is only intended for a limited group of recipients.
-
Authenticity means genuineness in the sense of originality.
-
Integrity means intactness, i.e. that data is protected from unnoticed alteration.
-
Binding obligation requires the inadmissible denial of any actions performed (e.g. conclusion of a contract) to be impossible. Electronic signatures are a means of creating binding obligations.
Symmetric and asymmetric encryption
Encryption is used to protect a communication (or in general: data) from being intercepted, i.e. to ensure confidentiality.
‘Symmetric’ encryption is the classic method. In this case, a key, i.e. a secret, is used that is known to all communication partners. This secret must therefore be disclosed to these partners in advance. Symmetric encryption methods have been in use for thousands of years. Well-known examples from ancient times include the Caesar cipher or the scytale of the Spartans, while other examples date back to the Ancient Egyptian or Mesopotamian empires. It is therefore an age-old technique.
Example of the Caesar cipher
This example involves replacing each letter of a message with the next letter in the alphabet. This is referred to as a ‘substitution’. Example: The word ‘CAESAR’ becomes ‘FDHVDU’.
Example of the scytale
The scytale is a wooden stick with a standardised diameter. A strip of leather or parchment was wrapped around it, with the secret message written on this. This strip was unwound and transported without the stick, meaning that the tape contained a seemingly arbitrary sequence of letters. Since the recipient of the message had a scytale of the same size as the sender’s, they could read the message by wrapping it around their own scytale. This method is also referred to as ‘transposition’.
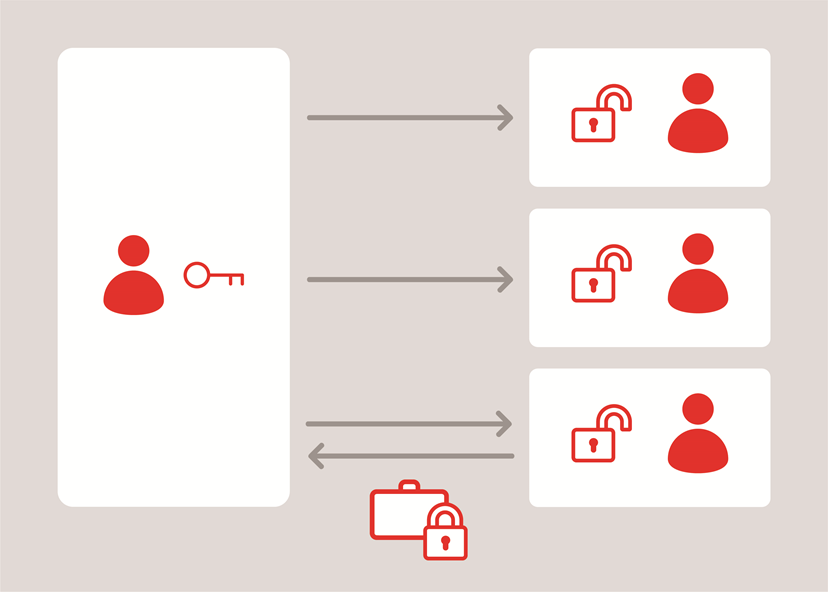
‘Asymmetric’ encryption does not use a common secret, but rather a key pair. This consists of the ‘private’ key and the ‘public’ key derived from it. The public key vhas its name because it can be published and be publicly available. The public key can be used to encrypt data. The private key, as the name suggests, must be kept secret and decrypts the data encrypted using the public key.
The first asymmetric methods were developed in the 1970s and were used with computers right from the outset. Public keys can be exchanged on an ad-hoc basis, including between participants or parties that do not know each other and have not exchanged keys beforehand. This method is therefore predestined for non-exclusive open user groups that interact on the internet.
Public key method
Asymmetric or public-key-based methods are based upon mathematical operations which can be calculated in an easy way in one direction, while the inversion generates such a high computational effort that it is impossible to perform in practice. These are also referred to as ‘trapdoor’ or ‘one-way functions’.
RSA
The most widely used and well-known asymmetric method is the RSA method. RSA stands for ‘Rivest, Shamir, Adlman’, the names of the inventors of this process. The one-way functionality of the RSA method is based on the fact that two prime numbers can be easily multiplied by each other. If only the product, i.e. the result of the multiplication, is known, a lot of work is needed to break this number down into the two prime number factors. If the numbers are large enough, this ‘factorisation’ is impossible. The private key is derived from the two prime numbers, while the public key is derived from the product.
PKI in practice: digital signature or proof of identity
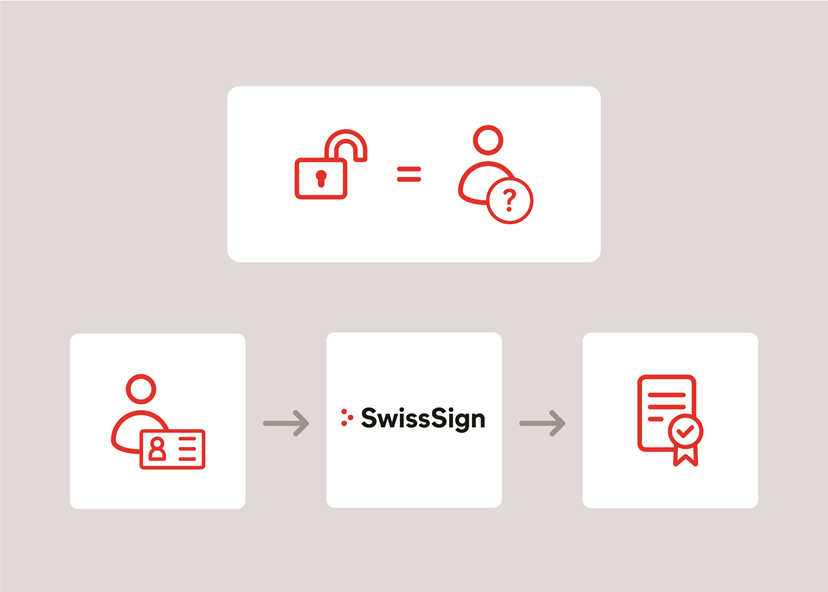
The above explanations have dealt with the technical, cryptographic basics. But they have not answered how to ensure who owns a key pair. This is where public key certificates come into play. These are issued by a trusted third party and they link a public key to an identity, i.e. to the owner of the associated private key. This keyholder may be a person, an organisation, a technical address or a machine or device.
-
Counterfeit-proof electronic signatures for documents or data in general. This can be done, for example, in the same way as a handwritten signature or as a ‘seal’ by an organisation.
-
Authentication, i.e. proof that someone is who they claim to be (in the same way as presenting an identity document in the physical world).
PKI in practice: certificates, the registered binding of a public key to an identity
The above explanations have dealt with the technical, cryptographic basics. But they have not answered how to ensure who owns a key pair. This is where public key certificates come into play. These are issued by a trusted third party and link a public key to an identity, i.e. to the owner of the associated private key. This keyholder may be a person, an organisation, a technical address or a machine or device.
The technical standard for the format of these certificates is ‘X.509’. The X.509 standard is maintained by the International Organization for Standardization (ISO) together with the International Telecommunication Union (ITU), both based in Geneva.
The identity must be registered properly
The identity in the certificate must always be verified and registered correctly andwith an audit trail. Brand-new cryptographic and technical advances are useless if the registration processes can be tricked. Proper registration or ‘validation’ is therefore at least as important as the technical controls – and corresponding effort is required. This is by no means unnecessary bureaucracy and hassle.
PKI hierarchy: certification authority
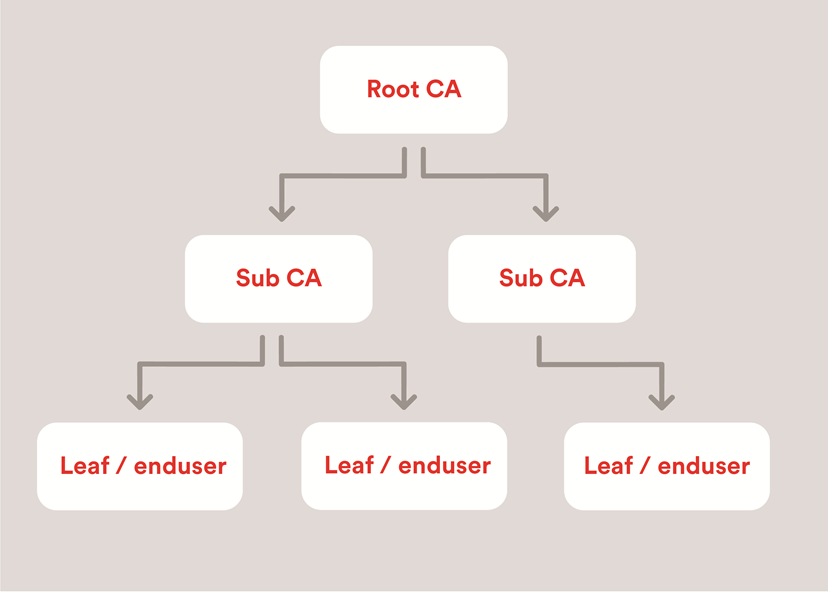
A PKI for X.509 certificates follows a strict hierarchical structure. It is a ‘tree’ in the sense of computer science or graph theory. A root is the highest element, while the lowest elements are the leaves of the tree. A body that issues certificates is a ‘Certification Authority’, also known as a ‘Certificate Authority’, abbreviated to CA.
The Root CA only issues a few certificates for the sub-CAs. These in turn issue the Leaf certificates, which is why they are also referred to as ‘Issuing CAs’. Leaf certificates are typically used by end users, i.e. customers of the CA.
The arrows in the graphics above represent a trust relationship and the CA issuing a certificate has verified the identity in the certificate as described above. In technical terms, the CA implements this trust relationship by digitally signing the certificate data. The root certificates are usually included in a ‘rootstore’, a database of trusted root certificates. Rootstores are pre-filled according to predefined rules and delivered within operating systems, browsers or email clients. Thanks to the trust relationships described and their transitivity, if a Root CA is trustworthy, with this concept millions of end-user certificates issued under it can also be trusted.
Validity of X.509 certificates
All certificates have a certain period of validity, i.e. a beginning and an end of validity. However, it is possible for a certificate that it shall not be used anymore before the originally set expiration date. Reasons for this may be, for example, that the identity information is no longer correct, that the certificate has already been replaced or, in the worst case, that the private key is no longer secure. CA providers therefore provide services for the revocation of certificates.
The information regarding the status of the certificates (‘valid or revoked?’) is published by a CA. This takes the technical form of a publication containing a list of revoked certificates, known as a ‘Certificate Revocation List’ (CRL). Another method for notifying the validity status is the ‘Online Certificate Status Protocol’ (OCSP), which is used to query the revocation status of individual certificates. However, OCSP is becoming less significant, especially with SSL/TLS certificates, due to its technical complexity and vulnerability to malfunctions, as well as concerns about privacy, particularly when handled incorrectly.
Shortening validity periods: a growing challenge
The validity periods of public SSL/TLS certificates are being continuously shortened. Since June 2024, the maximum term has been reduced to just 398 days. By 2029, it will drop further to just 47 days. This development poses significant operational challenges for businesses: certificates must be renewed more frequently, the risk of expired certificates increases, and the manual administrative effort increases significantly. Without automation, certificate management quickly becomes a time-consuming burden for IT teams. In our blog post on shortened TLS lifetimes, you can find out what these changes mean in concrete terms and how you can prepare for them. An effective solution is Certificate Lifecycle Management (CLM), which fully automates the renewal, monitoring and management of your certificates – ensuring your IT security without additional manual effort.
What you need PKI (public key infrastructure) for
Companies use PKI as follows to benefit from the security enhancements and to speed up their processes – with our products, we at SwissSign offer the optimal solution for each case.
SSL or TLS certificates (SSL: Secure Socket Layer, TLS: Transport Layer Security)
When an encrypted connection is established to a web server on the internet, this server must be authenticated. This is necessary because a connection that is encrypted but established with the wrong server as communication partner is not confidential. To use the public key for encryption in the certificate is possible as well, but this is no longer considered best practice. The use of SSL/TLS is standard in modern internet browsers.
Go to our range of certificates
Secure email or S/MIME
X.509 certificates are used to secure email traffic on the internet. The associated technical standard is known as S/MIME (Secure/Multipurpose Internet Mail Extensions). The applications are:
-
S/MIME allows email messages to be signed and the authenticity of the sender to be ensured. In the age of spam and phishing emails, this kind of signature is valuable proof that an email has really originated from the alleged sender.
-
The use of a certificate belonging to a holder of an email address allows sending encrypted messages sent to them so that only they can read the email.
Go to our range of email certificates
Document signature by individuals
Just like with a paper signature in the physical world, a person can give their consent to a document by means of an electronic signature. By law, the ‘qualified electronic signature’ (QES) is equivalent to handwritten signatures in the physical world, but other types of signatures can also be used depending on the (formal) requirements.
Go to our services for digital signatures
Electronic seals originating from an organisation
One special case of electronic signatures is the electronic seal. Seals are signatures created on behalf of an organisation or a legal entity. They are particularly suitable for automated applications that exchange invoices or other important business documents. A seller's seal, for example, can be used to prove that an invoice is originally from the seller, as well as that the invoice amount and the stated VAT amount are correct.
Go to our services for digital signatures
Internet of Things
The Internet of Things (IoT) consists of physical devices, typically equipped with a sensor, that communicate with online services. One example is smart home devices, such as ‘smart metering’ for measuring electricity consumption or generation. Certificates are used to securely authenticate both the devices and online services.
Go to our range of device certificates
Windows PKI
Certificates managed in the Microsoft Active Directory (AD) are also used in an internal company Windows network. This kind of Windows PKI can be operated in-house or purchased as a cloud service.
Timestamping
The purpose of timestamping electronic documents is to prove the existence of an electronic document at a certain point in time. For this purpose, the service provider operates a service that receives requests and returns time confirmations or timestamps. It should be noted that the documents do not have to be disclosed to the service, with the submission of unique document identifiers (known as ‘hashes’) sufficient. Timestamping is used in the archiving of electronic documents.
How PKIs are regulated for maximum trust and security
The trustworthiness of a CA and the certificates it issues depends on its security level. This must be complied with comprehensively across all areas. Laws and standards, i.e. sets of rules and regulations, are in place that set out the requirements in this regard as well as with regards to its auditing. These include:
-
Governance, i.e. the management and regulatory system of the CA. This includes technical and organisational measures to protect the company, supervision, process maturity and liability regulations.
-
The level and nature of the registration (e.g. proof of ownership of a domain name for which an SSL/TLS certificate is issued by the applicant).
-
If applicable, specifications for the cryptographic token used, i.e. for protecting the private key associated with the digital certificate (e.g. storage within certified hardware).
Relevant regulators and regulations for SwissSign are:
-
CA/Browser Forum for regulating SSL/TLS and email certificates on the internet
-
Guidelines and policies of browser, email client and operating system manufacturers, i.e. Google, Microsoft, Apple and Mozilla
-
Swiss Federal Act on Certification Services in the Field of Electronic Signatures and Other Applications of Digital Certificates ‘ESigA’/'ZertES'
-
EU Regulation on Electronic Identification and Trust Services for Electronic Transactions in the Internal Market ‘eIDAS’
-
Adobe Approved Trust List (AATL)
-
PKI-specific standards of the European Telecommunications Standards Institute (ETSI)
Furthermore, as a Swiss provider that stores 100% of its data in Switzerland, SwissSign is of course also required to comply with all non-PKI-specific legislation in Switzerland. Given that SwissSign is also certified in accordance with the EU eIDAS Regulation and has built up a large customer base in the EU, various EU regulations are also relevant, in addition to the aforementioned eIDAS Regulation, e.g. the General Data Protection Regulation (GDPR).
Why should companies use a PKI?
PKI offers companies a reliable way to digitally secure and accelerate their communications and processes. For IT managers, choosing a PKI is an investment in the future – it creates security, efficiency and trust for all digital business processes.